Windows AD FS SSO
Amazon Cognito integrates with Windows Active Directory Federation Service to enable existing AD users to sign-on to Amorphic Data Cloud. This section explains how to register and set up your application with Windows AD FS as an identity provider.
What is Single Sign-On?
Single sign-on (SSO) is an authentication method that enables users to securely authenticate with multiple applications and websites by using just one set of credentials. SSO works based upon a trust relationship set up between an application, known as the service provider, like Amorphic Data Cloud and an identity provider, like Windows ADFS. This trust relationship is often based upon a certificate that is exchanged between the identity provider and the service provider. This certificate can be used to sign identity information that is being sent from the identity provider to the service provider so that the service provider knows it is coming from a trusted source.
Pre-requisites for Windows ADFS Identity Provider
Before we proceed with the Windows AD FS IDP setup, we need the following pre-requisites:
- Active Directory Federation Service configured, available under a given domain to public and a valid SSL certificate.
- Amorphic application deployed with Identity Provider option enabled
Steps to register Amorphic app with AD FS
Connect to the Windows instance using a Windows RDP client.
Add a claims-aware relying party trust in AD FS
Open ADFS Management Application and click on Relying Party Trust and click on Add Relying Party Trust option in the Actions pane
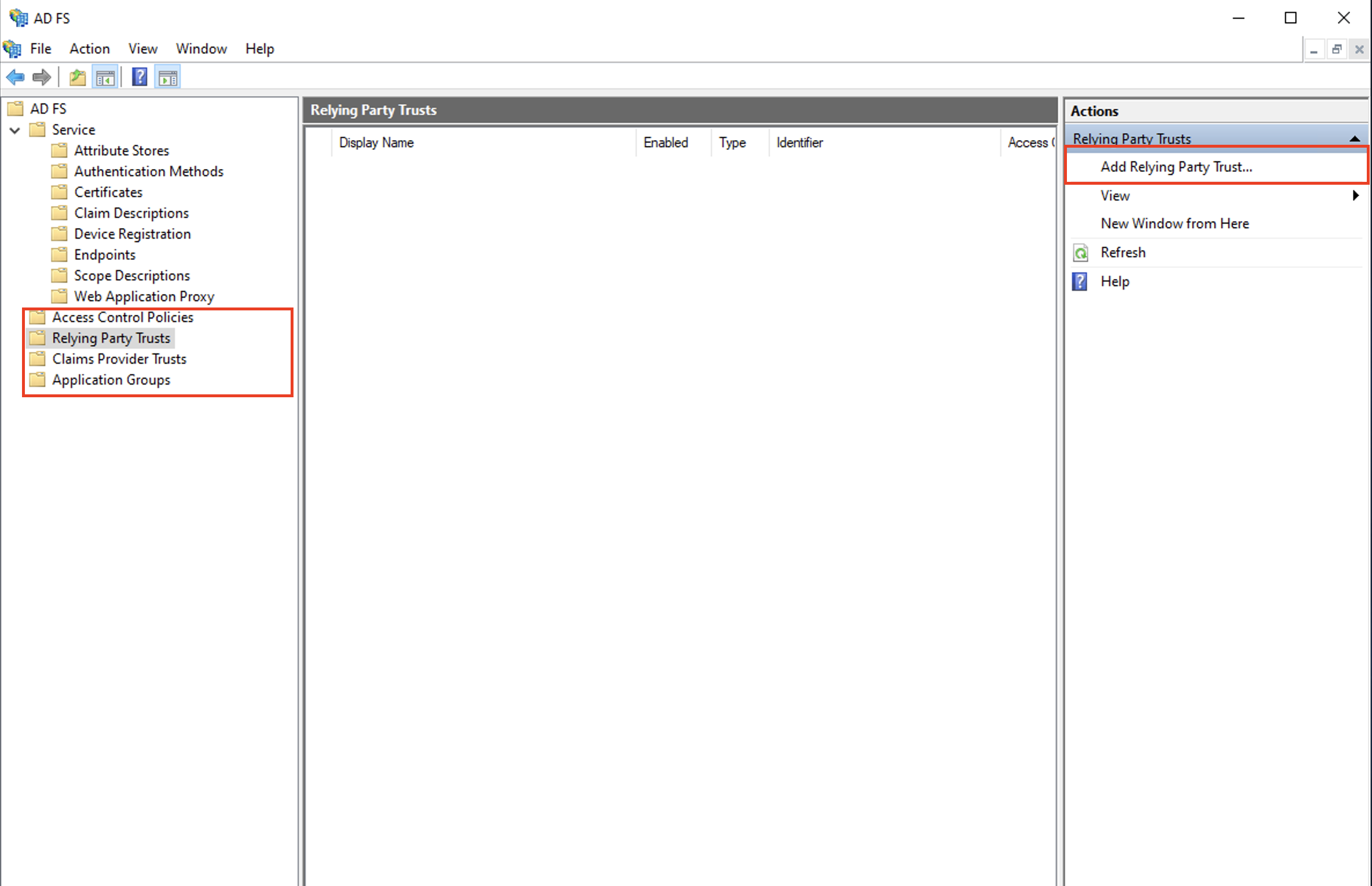
Select Claims Aware and click start
On the next page, select Enter data about the relying party manually option and click Next and specify a Display name on the next page.
On Configure URL page, select Enable support for the
SAML 2.0 WebSSO protocoloption and forRelying party SAML 2.0 SO service URLenter, formatted as follows:https://congnitodomain.auth.region.amazoncognito.com/saml2/idpresponse. Replace congnitodomain with your Amazon Cognito user pool's domain prefix and replace region with the user pool's AWS region
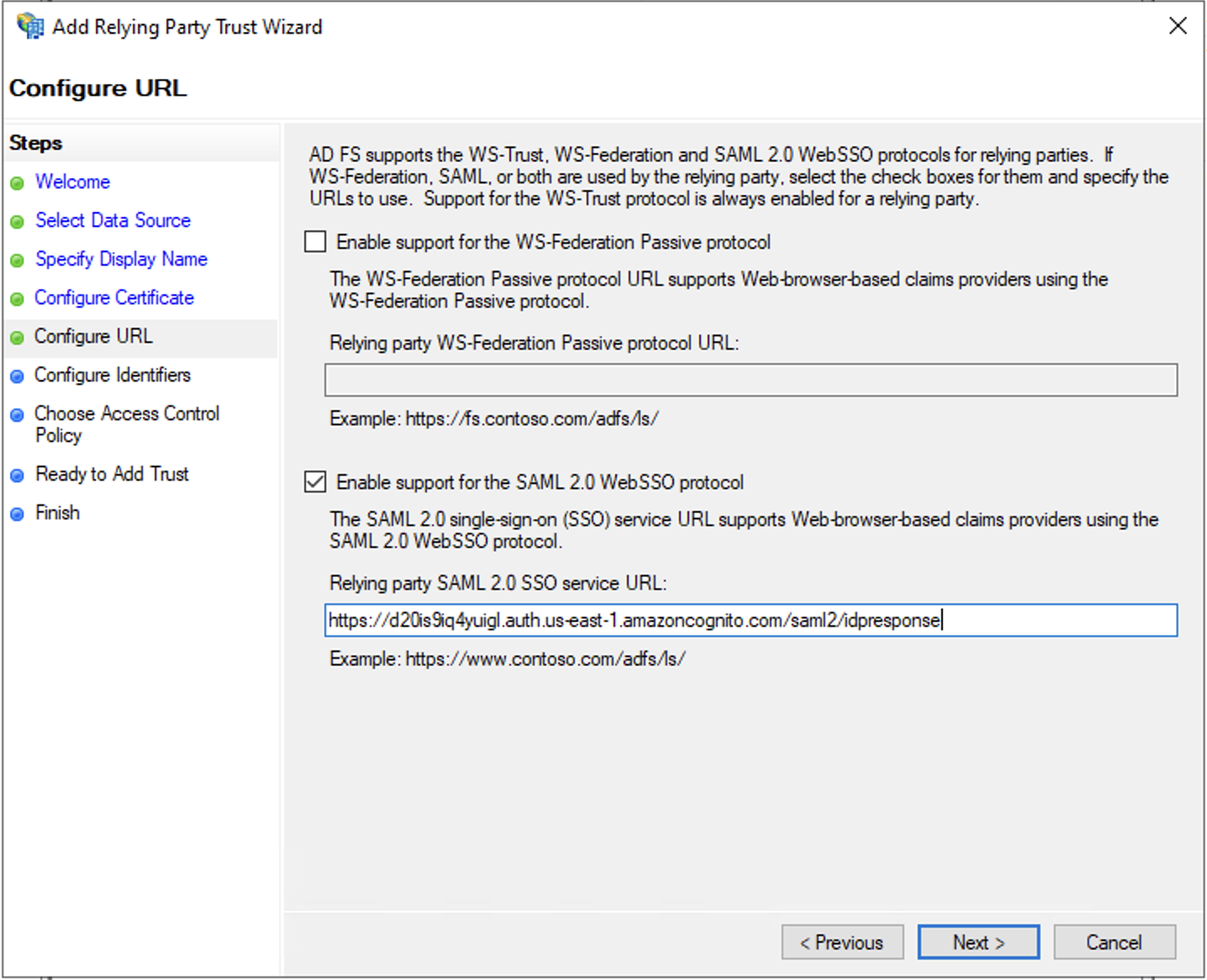
For
Relying party trust identifier, enter this URN:urn:amazon:cognito:sp:your_user_pool_id. Cloudwick support team can provide the cognito domain and userpoolid. Click on Add button and then Next button.Choose
Permit everyonepolicy and click Next and keep the rest default.Now you can see that a Relying Party trust has been created.
Edit application's claims issuance policy in AD FS
- Add a rule to the trust created above, to send LDAP attributes as claims. Amorphic requires 3 claims in the SAML response - name, username and email. Select the newly created trust and click on
Edit Claim Issuance Policy�option.
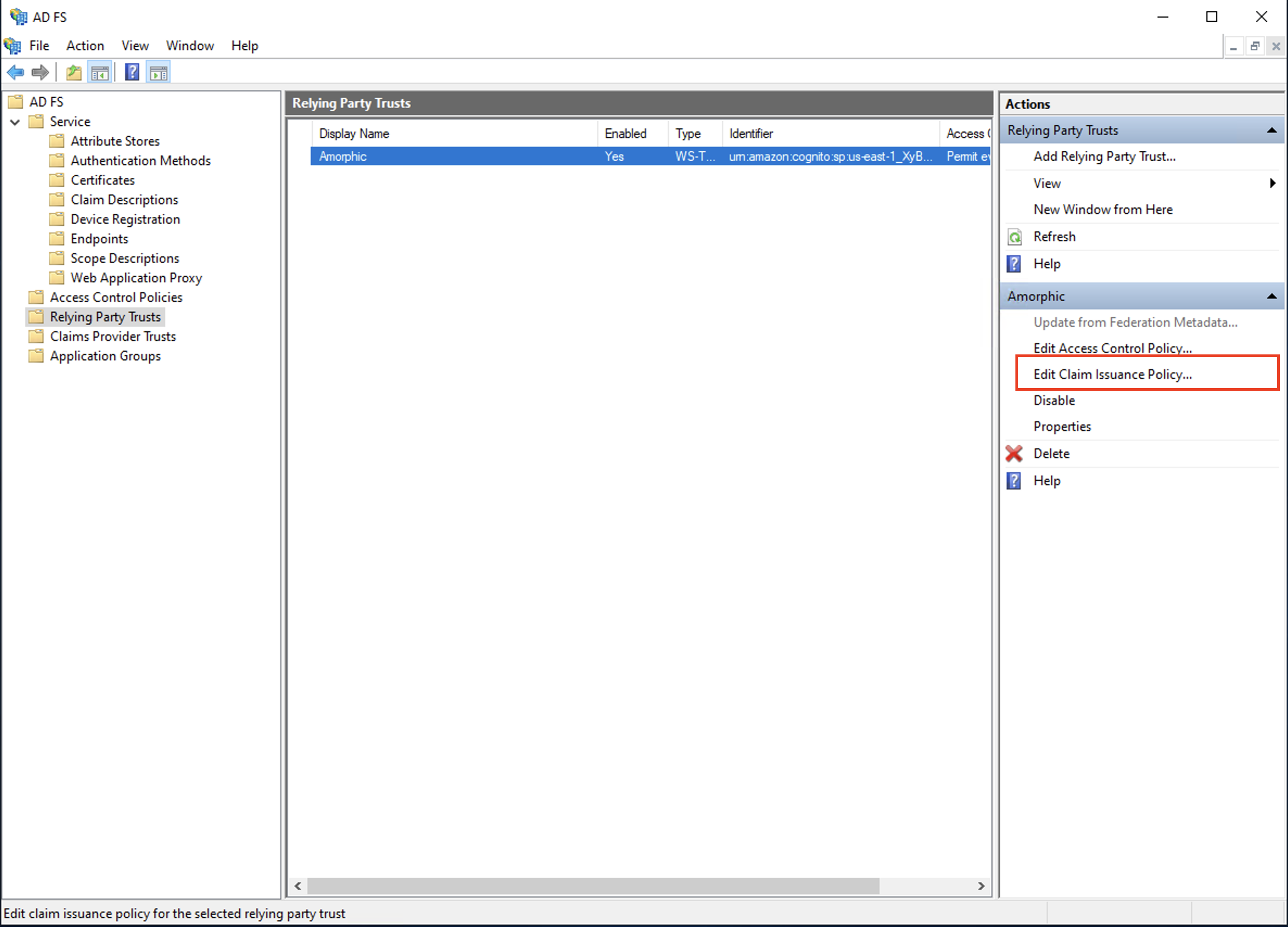
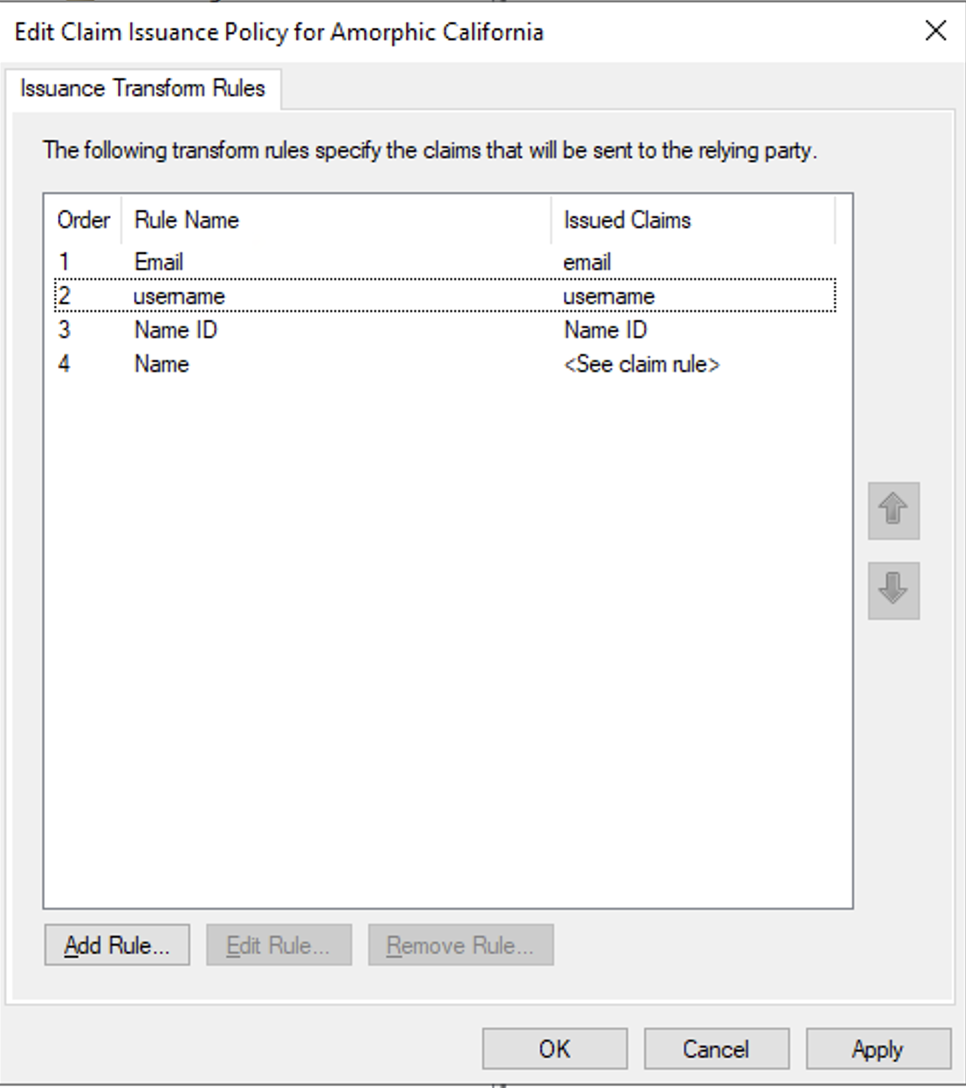
Click on Add New Rule, then for Claim rule template select
Send LDAP Attributes as Claimsand click Next ForClaim rule name, enterName ID. ForAttribute store, chooseActive Directory. ForLDAP Attribute, chooseSAM-Account-NameFor OutgoingClaim Type, chooseName IDRepeat the same for Email. For
Claim rule name, enterEmail. ForAttribute store, chooseActive Directory. ForLDAP Attribute, chooseE-Mail-Address. For Outgoing Claim Type, typeemailin small cases. Do not select Email from the list instead.Repeat the same for Username. For
Claim rule name, enterUsername. ForAttribute store, chooseActive Directory. ForLDAP Attribute, chooseSAM-Account-Name. ForOutgoing Claim Type, typeusernamein small cases.To add Name in SAML claims, click on Add, then select
Send Claims Using a Custom Rulefor Claim rule template. ForClaim rule name, entername. Forrule, enter the following.
c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"]
=> issue(store = "Active Directory", types = ("name"), query = ";displayName;{0}", param = c.Value);
- Click on Apply button and then Ok button
Update Amorphic with credentials
- In Amorphic CMP (customer management portal), select IDP provider as SAML and update the values.
IDP Server URLin cmp corresponds tohttps://<domain_name>/adfs/lsIDP Metadata URLin cmp corresponds tohttps://<domain_name>/federationmetadata/2007-06/federationmetadata.xml
Once the values are added, click on Update IDP Details.
This will take around 45-60 mins to get reflected in the login page.
