Roles
Role-Based Access Control (RBAC) in Amorphic is a feature that helps system administrators manage user access to sensitive information and reduce the risk of data breaches. This feature allows administrators to control which users have access to which services within the application, making it more efficient to authorize users and align with user management compliance. Amorphic RBAC is designed to be adaptable and support any new services that are added to the application, making it more versatile and useful.
Amorphic RBAC provides the following capabilities:
- User can have multiple roles attached and has the ability to switch between them to perform various actions based on his/her responsibilities.
- Customize user role permissions to a granular level. User can select from three levels of permissions: full access, manage and view.
- Flexibility to choose the type of Amorphic view upon login.
What is a Role?
In Amorphic, a role determines the level of access a user has in the Amorphic application.
RBAC improves data security by limiting users’ access to sensitive information and helps with compliance. Additionally, it allows users to switch between different roles to perform different tasks.
Role has the following properties:
- A Role can have multiple users attached to it.
- A Role can have many permissions.
- A Role can have multiple role managers who can perform update and delete operations on the role
In Amorphic, we have two types of Roles:
- System Roles : Which are provided by the application by default.
- Custom Roles : Created by users.
System Roles
Amorphic has two main roles: "Administrator" and "Regular User." Administrators have full access to all features and can perform all actions in Amorphic. While, regular users have basic access and can only perform certain actions. Additionally, every user has a "default role" which determines what they see when they first log in.
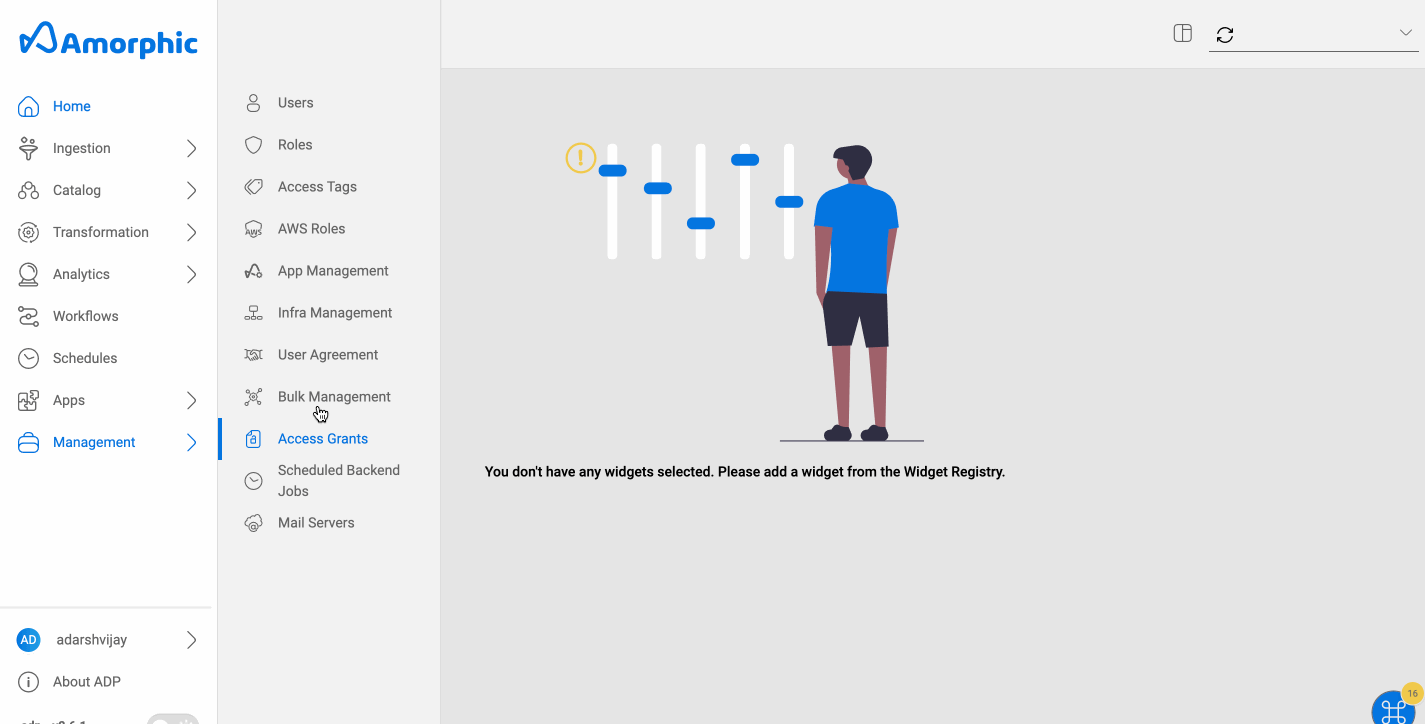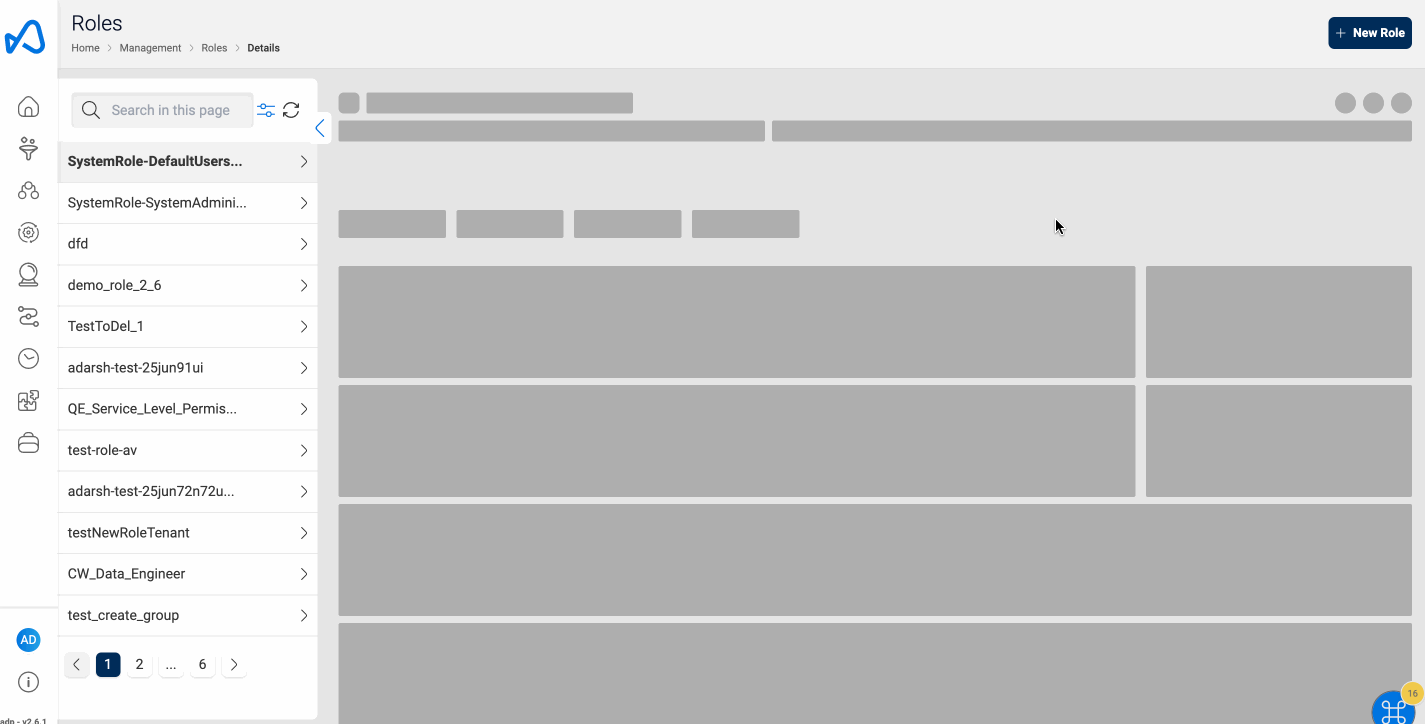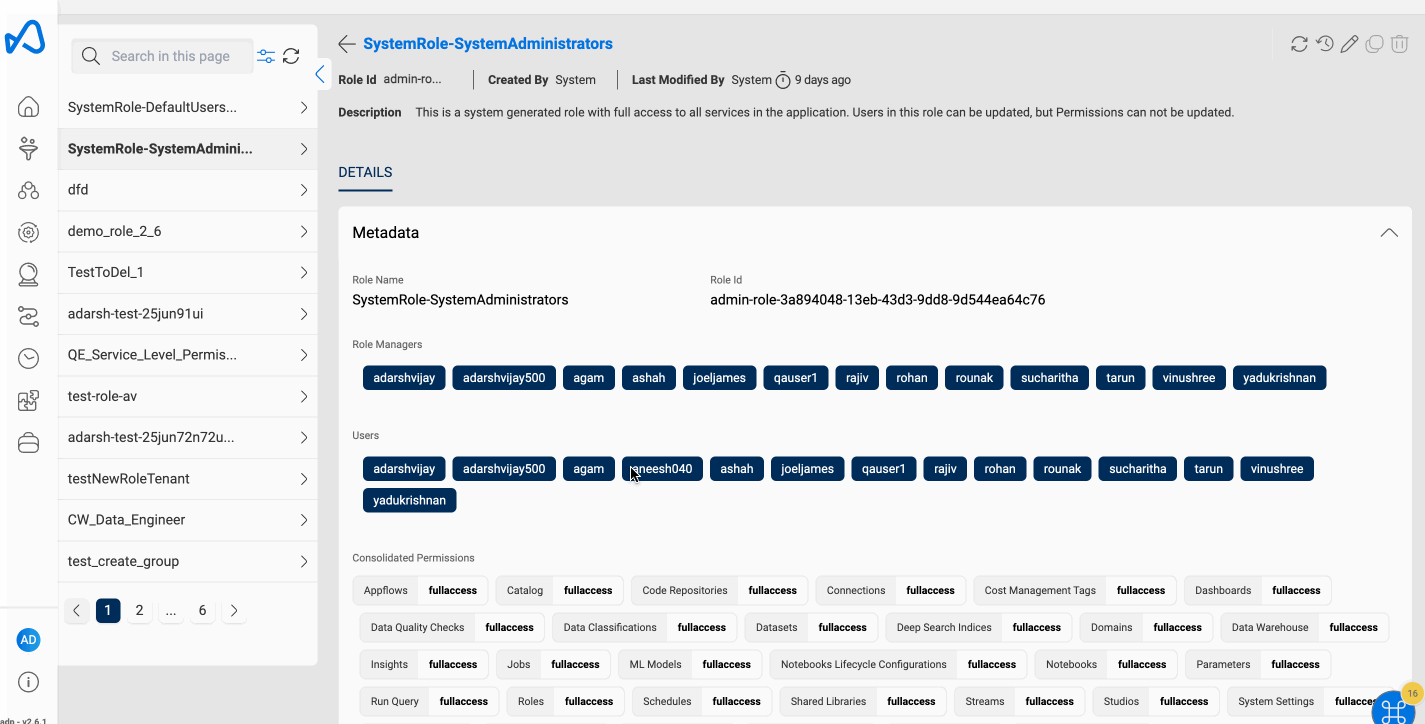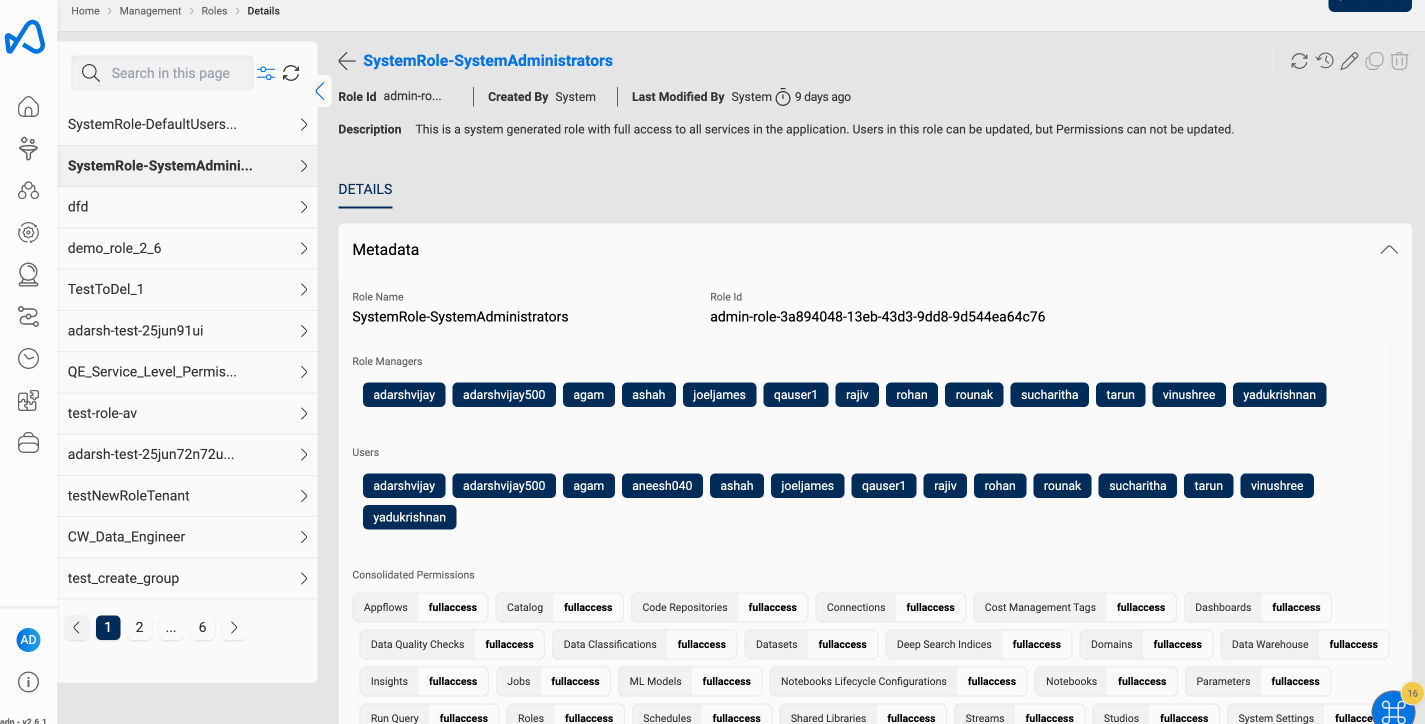
System Administrators Role This role consists full permissions for every service offered in Amorphic and can perform all the activities without any restrictions.
System Default Users Role System default Users Role is a basic application access role which is provided to every user.
This is not to be confused with user's default role. User's default role determines what all services that he/she sees when logged in.
Custom Roles
You can create a custom role for a user by selecting permissions from a list of specific access permissions for each service. To create a role see, how to create a Custom Roles
For Example, A user can create custom Data scientist role and provide access to only ML notebooks.
Amorphic RBAC Role contains the following information:
Role Metadata Information
| Type | Description |
|---|---|
| Role Name | The unique name identifying the role's functionality. |
| Role Description | A brief explanation of the role's purpose. |
| Permissions | Specific actions defined for a particular service. Permissions determine the level of access within Amorphic. Permissions can be assigned to multiple roles and vice versa. |
| Role Managers | The list of users who can update or delete the role |
| UsersAttached | The list of users to whom the role is attached. |
| CreatedBy | The user who created the role. |
| LastModifiedBy | The user who last updated the role. |
| LastModifiedTime | The timestamp of the last time the role was updated. |
Role Operations
Along with Amorphic RBAC, you can perform basic CRUD operations (shown in the below table) on a role if you have sufficient permission.
| Functionality | Description |
|---|---|
| Create Role | Create a custom role by choosing from a list of permissions and attach to a User. |
| View Role | View existing Role Metadata Information |
| Update Role | Update an existing role. |
| Delete Role | Delete an existing role. |
| Switch Role | This functionality helps user to switch between multiple roles attached. |
| Update User Default-Role | Helps user to customize the landing page view. Example: if User frequently uses Machine learning services, one can pick say a "Data scientist Role" as default login view for quicker access. |
- From v2.6, only a role's managers can update the role or delete it. The user who creates a role automatically becomes a role manager. Users can list or view a role only if they are a role manager or if they are attached to the role. Even if a user's role has the roles.update and roles.delete permissions, they will not be able to update/delete a particular role unless they are a role manager for that role.
- For roles existing before v2.6, all users having the system administrator role will become role managers.
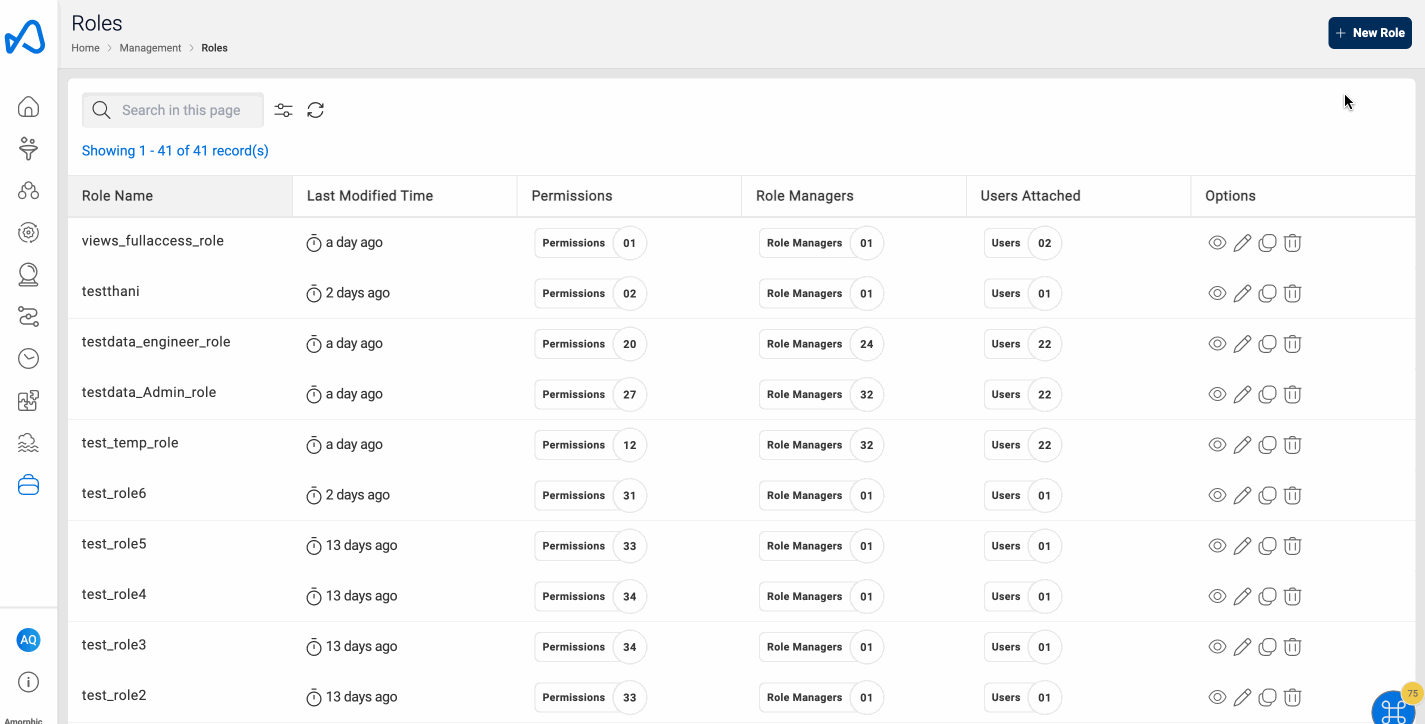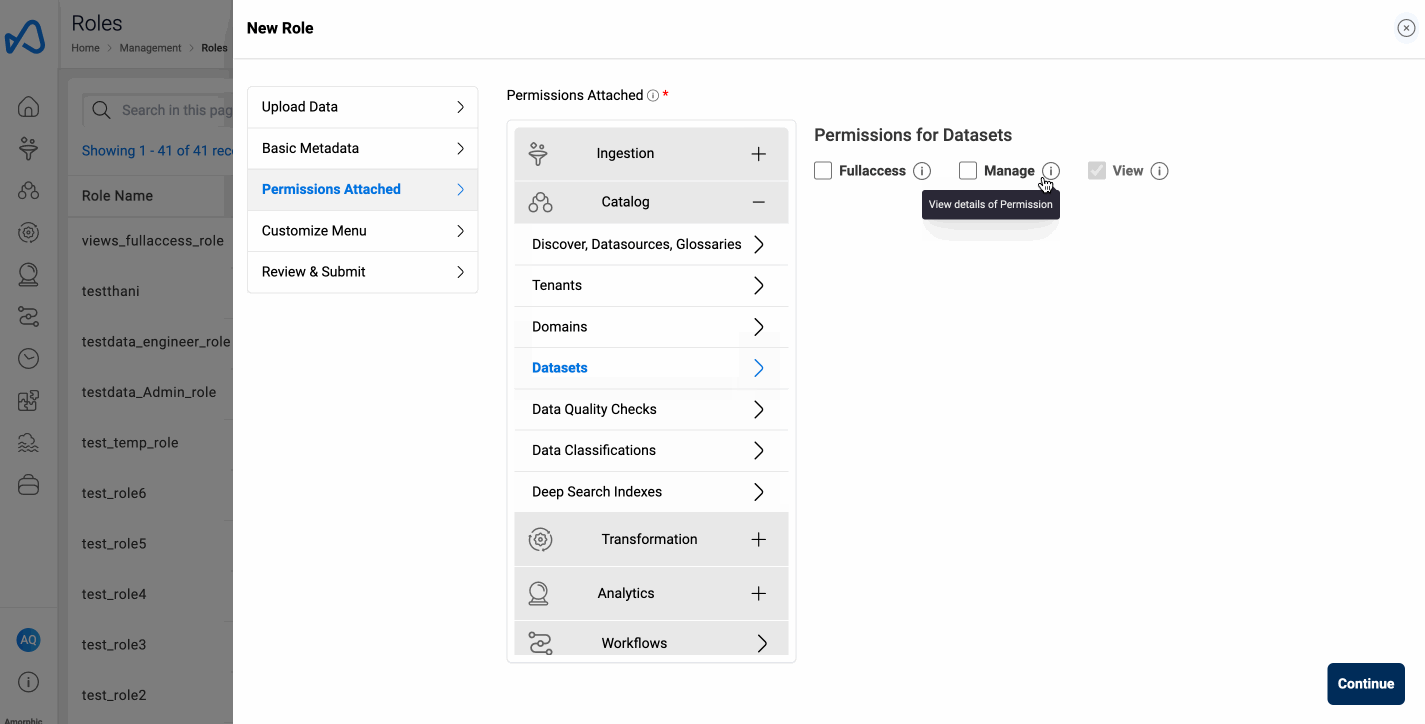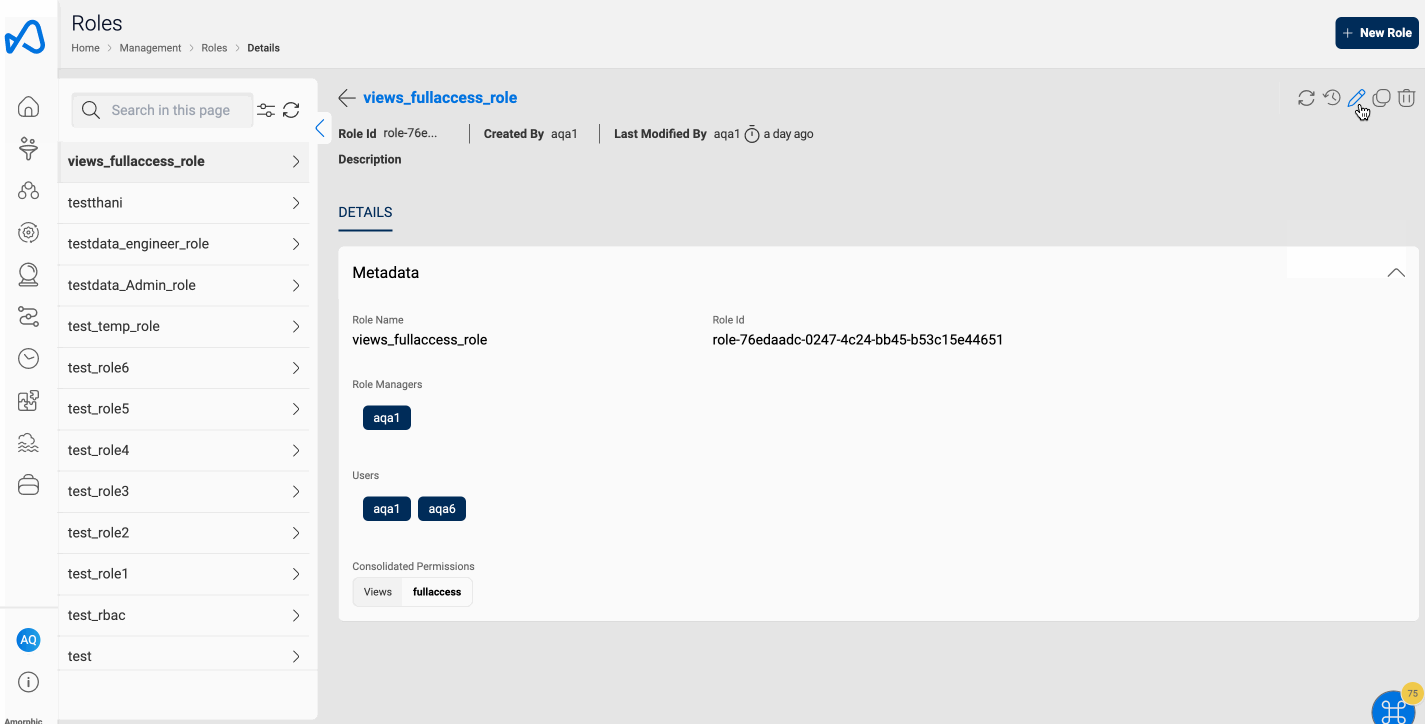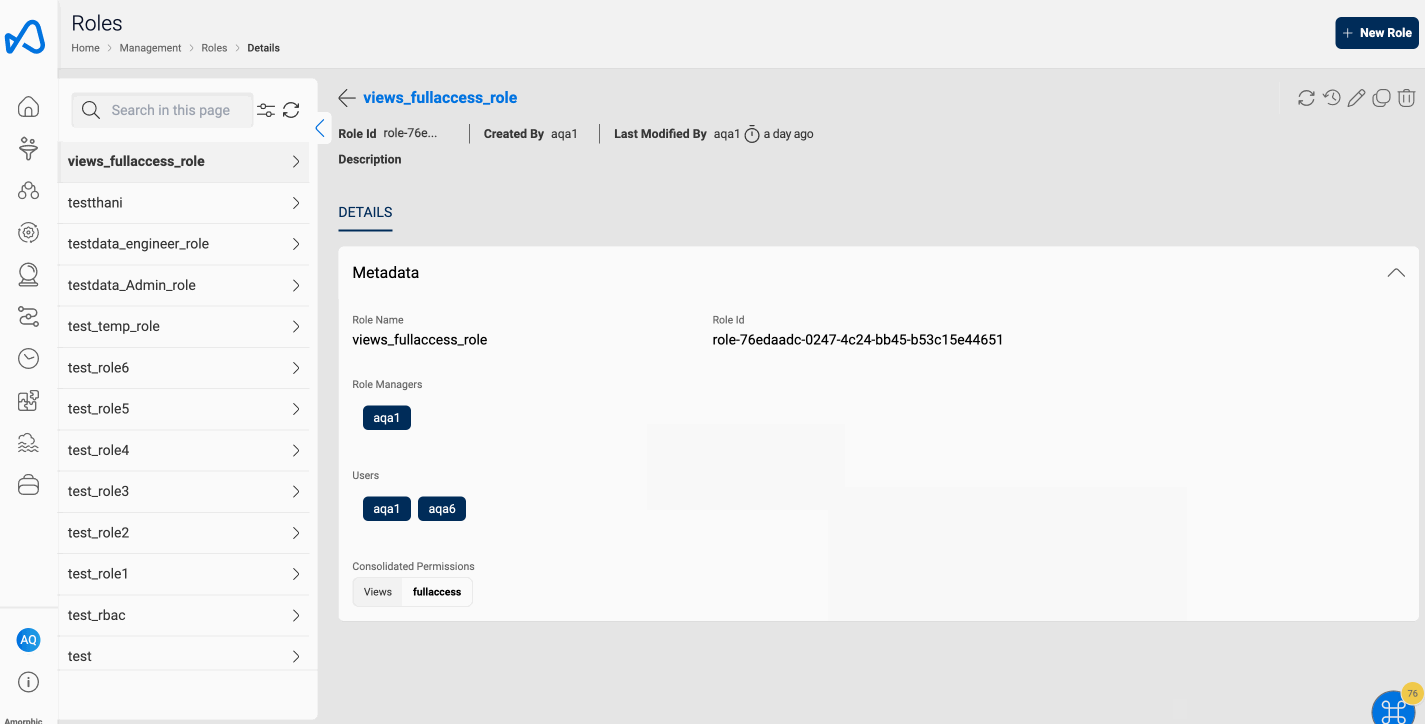
Create Role
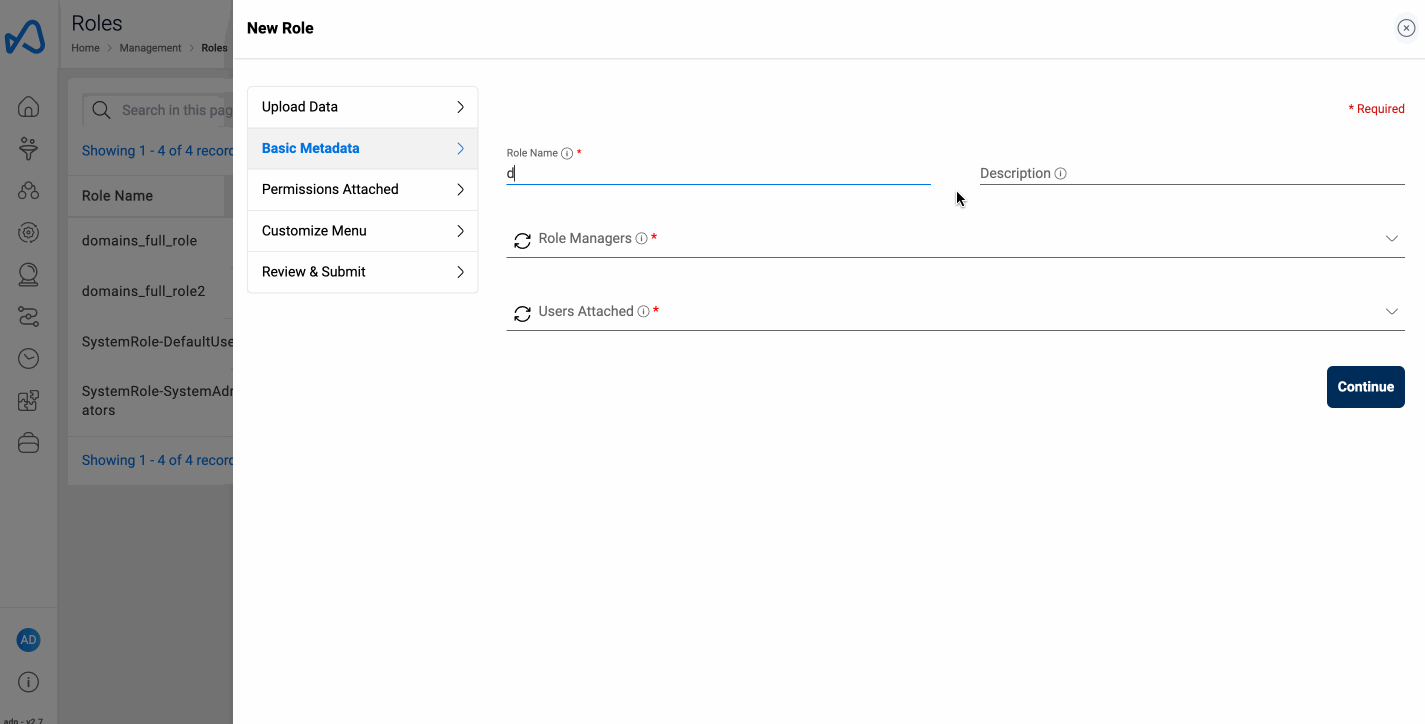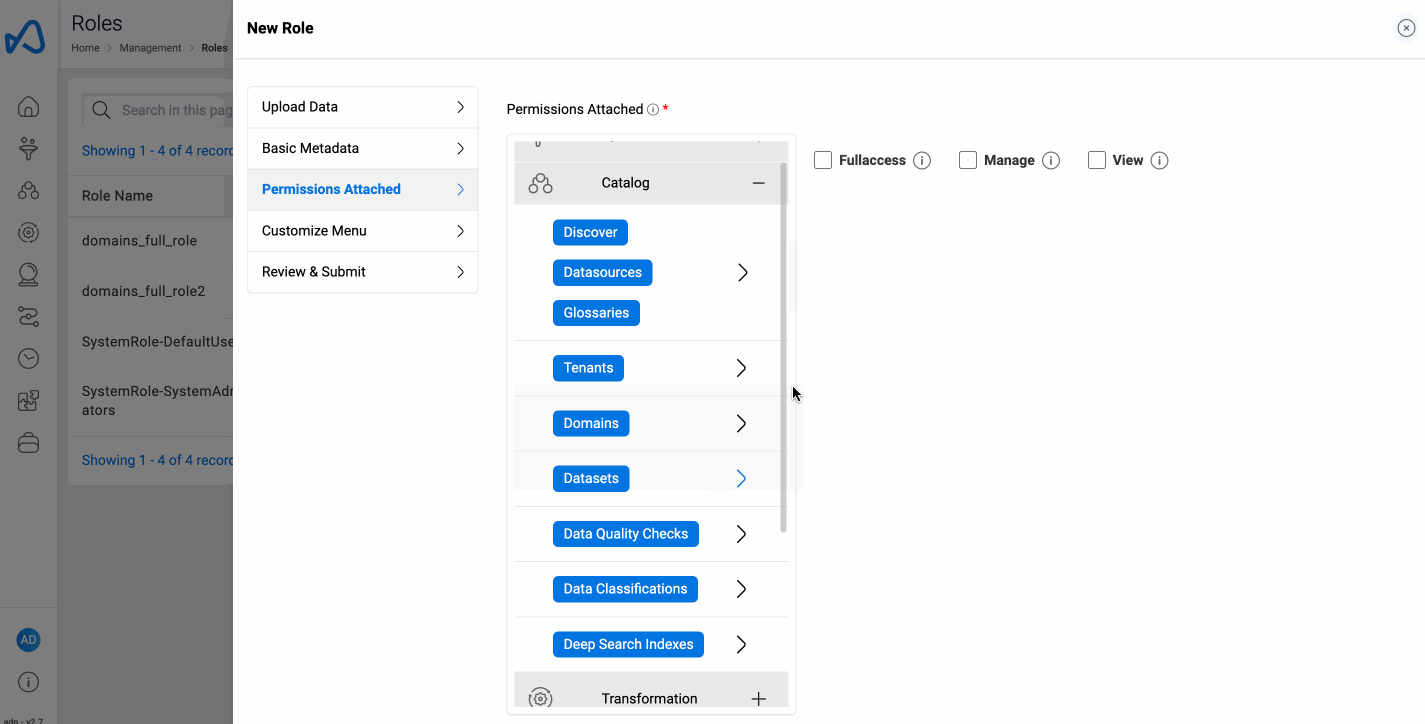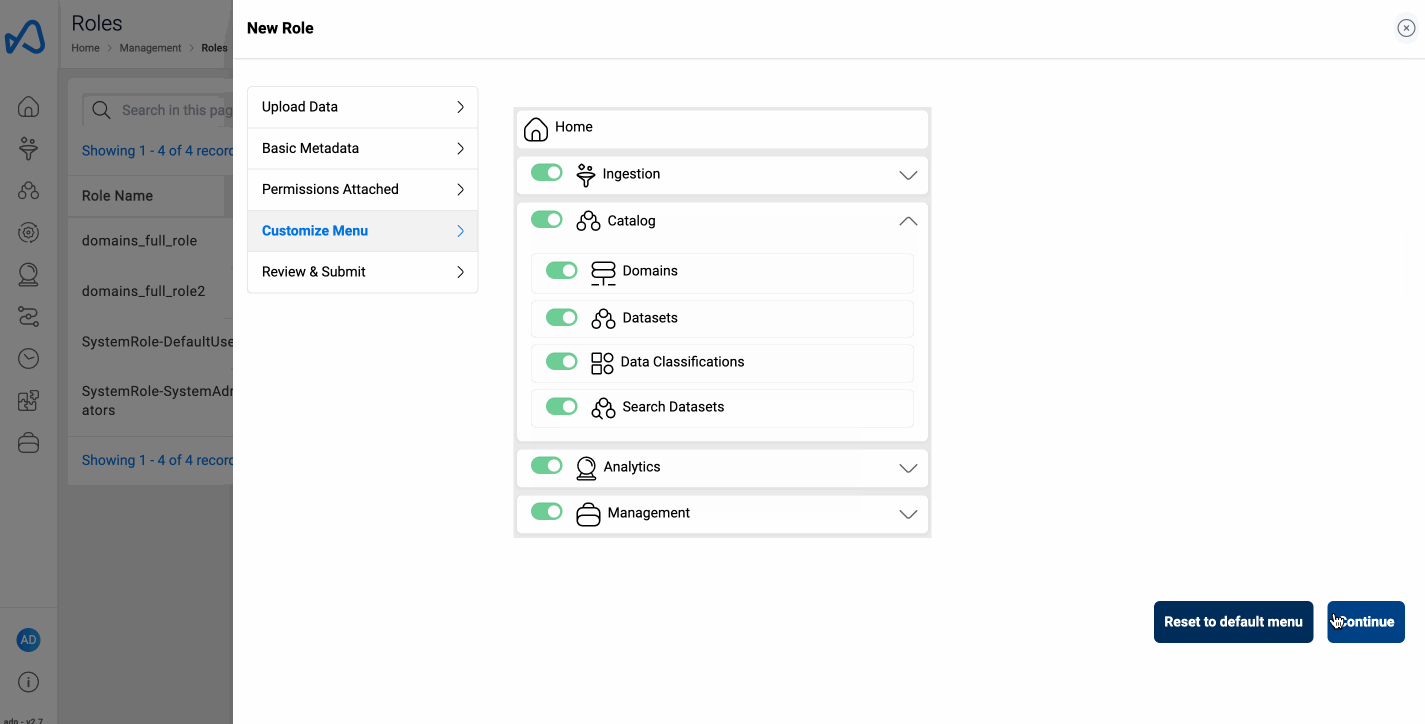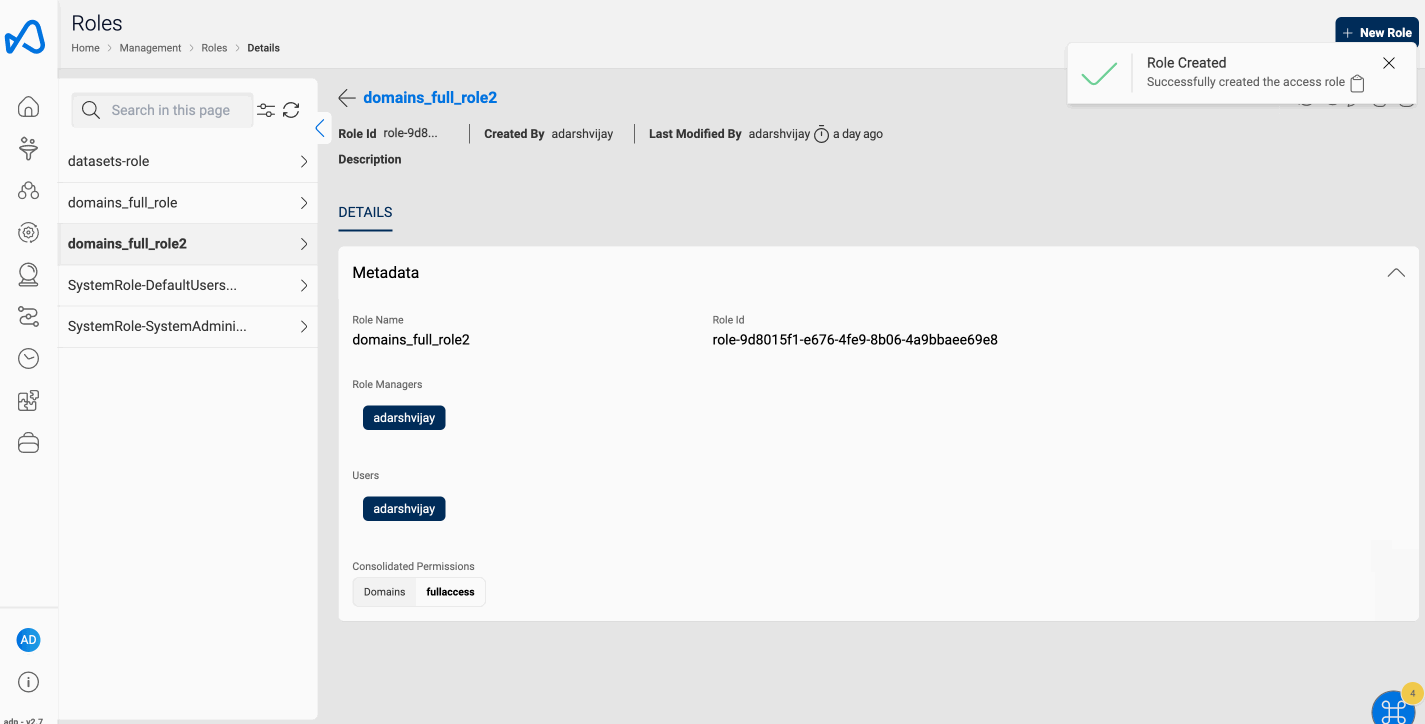
To create a new role in Amorphic, follow these steps:
- Go to the
Managementmenu and selectRoles. - Click on the
New Rolebutton. - Fill in the information required, such as role permissions and user names who will be attached to the role.
- Drag and Rearrange the order of your resources to be accessible in the sidenav.(User Persona)
- Click on
Createto create the new role.
User Persona
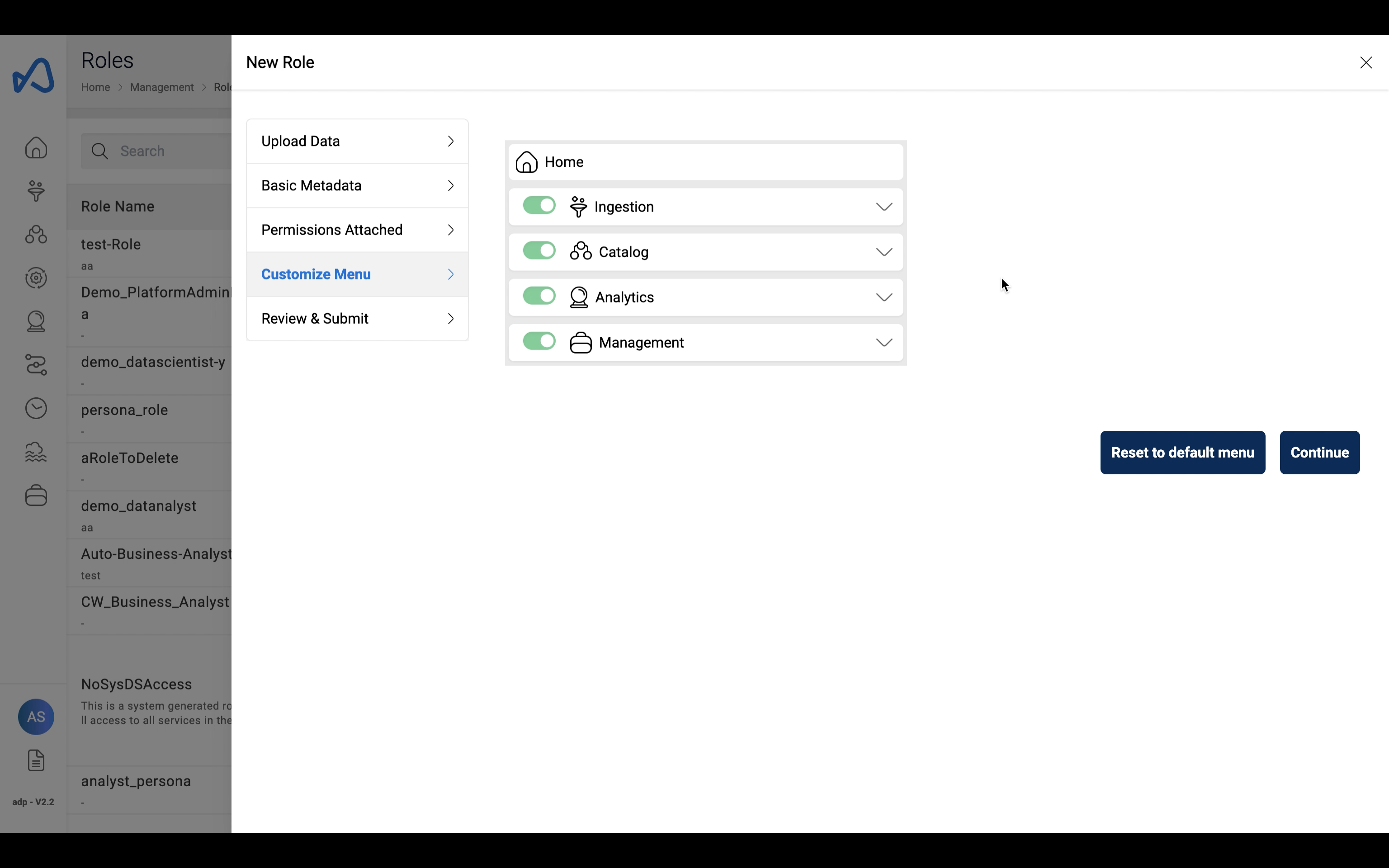
This section lets a user customize their sidenav to display only the resources that will be used by the user using the corresponding role that is being created/updated.
- User can drag and drop and rearrange the resources according to the user's preferences.
- User can toggle on/off submenus or individual resources to be shown in the sidenav.
- Resources will be displayed only if the user have their respective permissions.
- User can reset the order of the resources by using the
Reset to default menubutton.
There are no permissions specifically for Bulk Management.
Currently we only manage datasets so the bulk management page is only available for users with the datasets.update permission
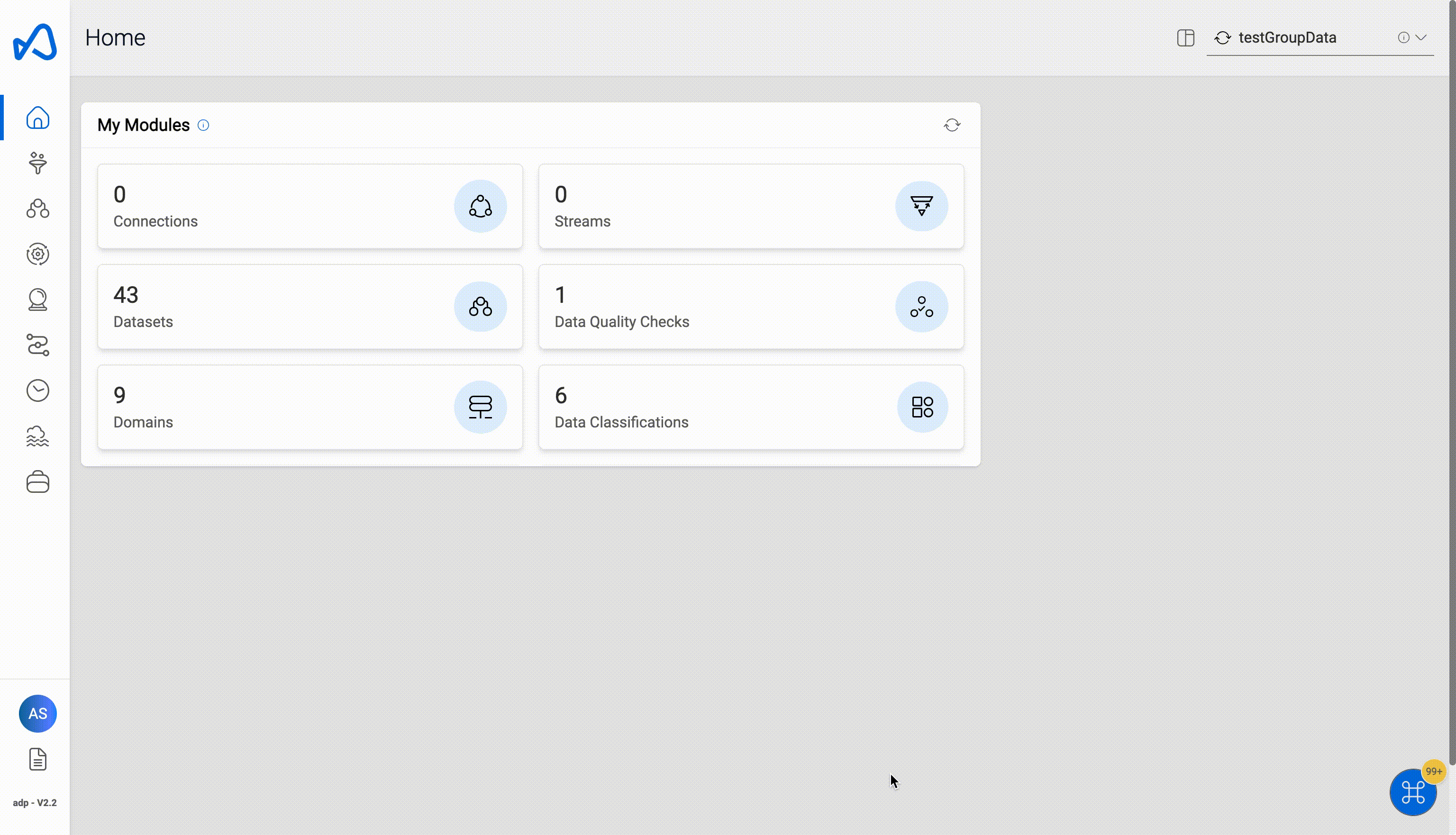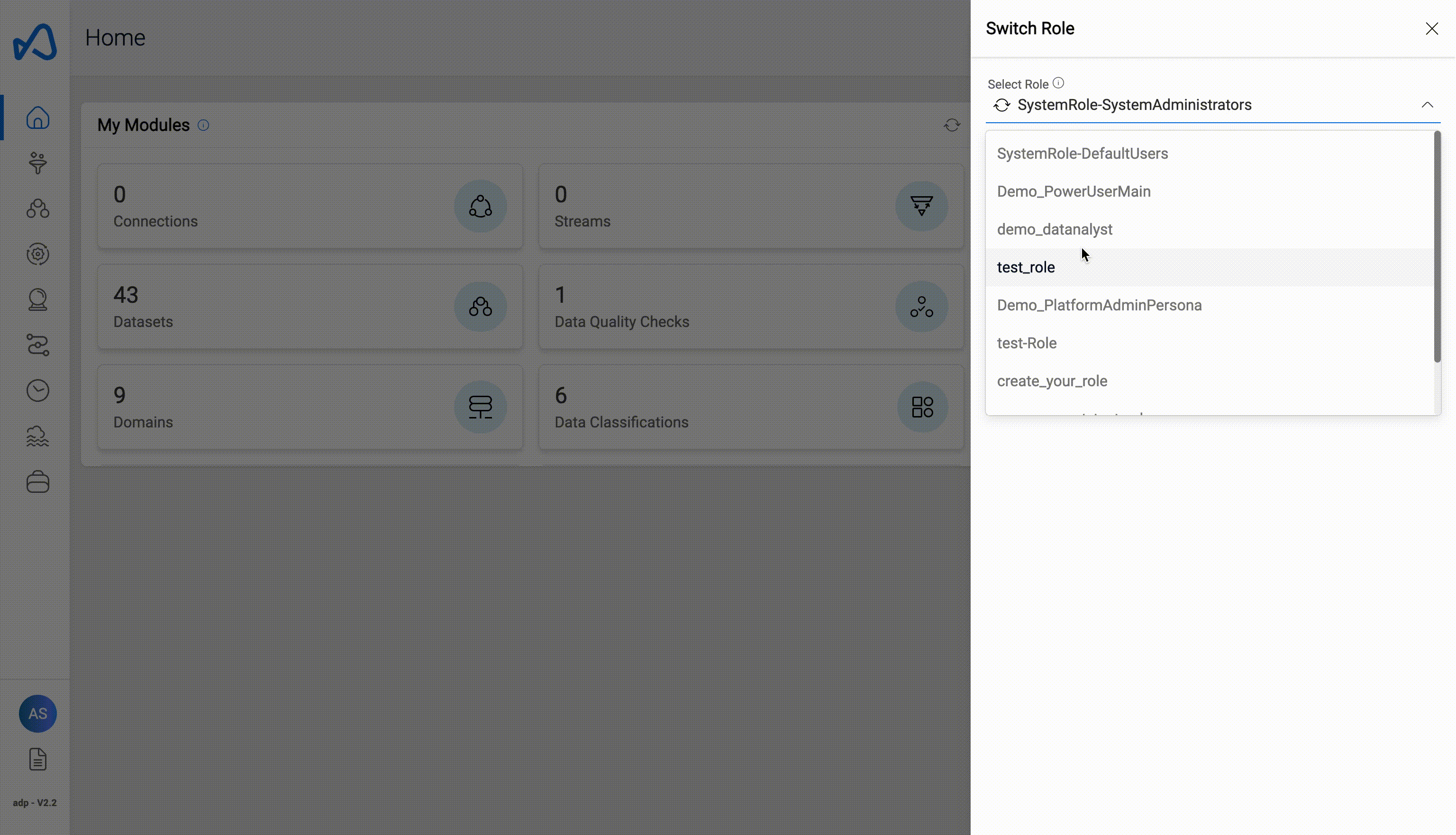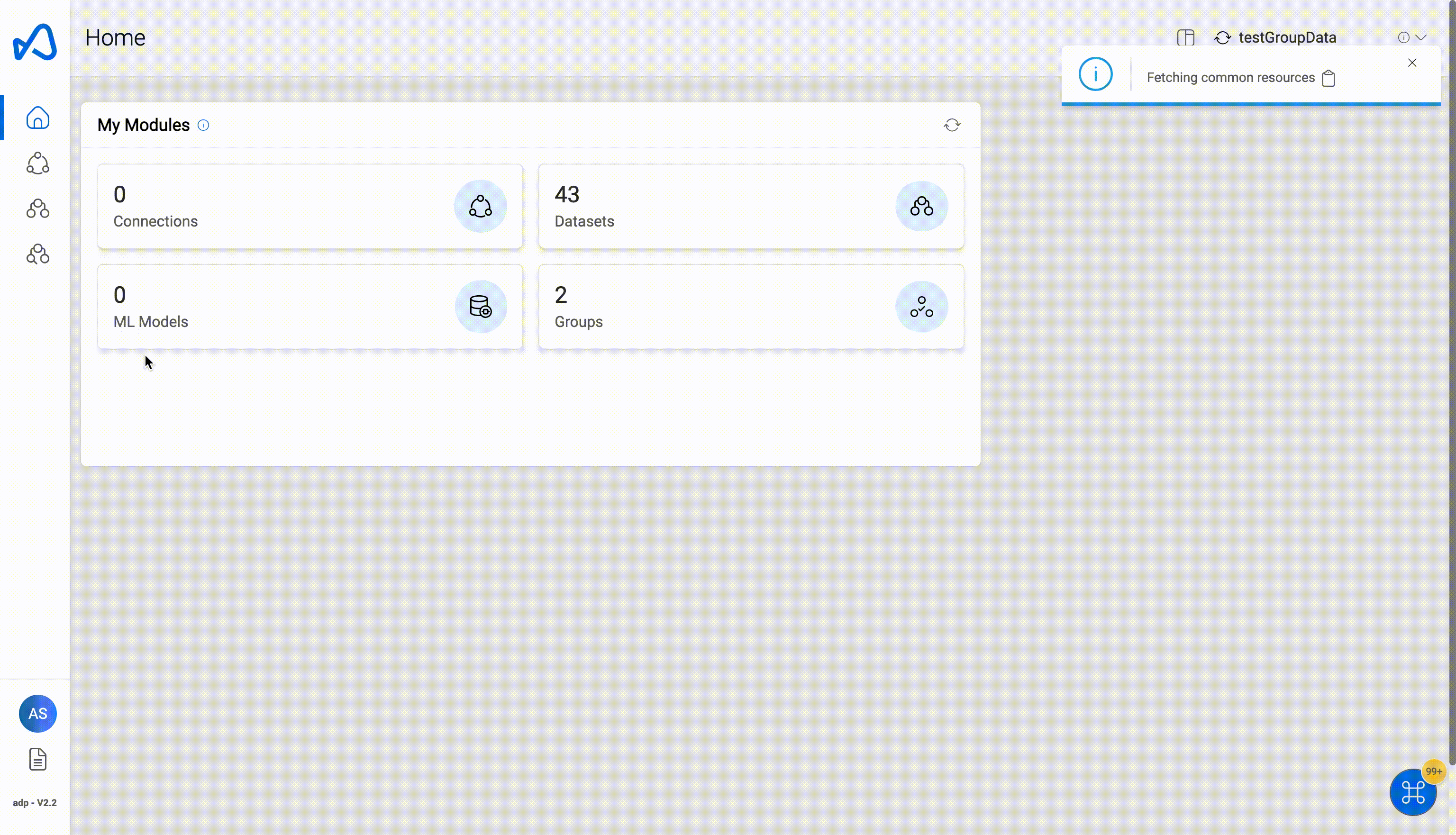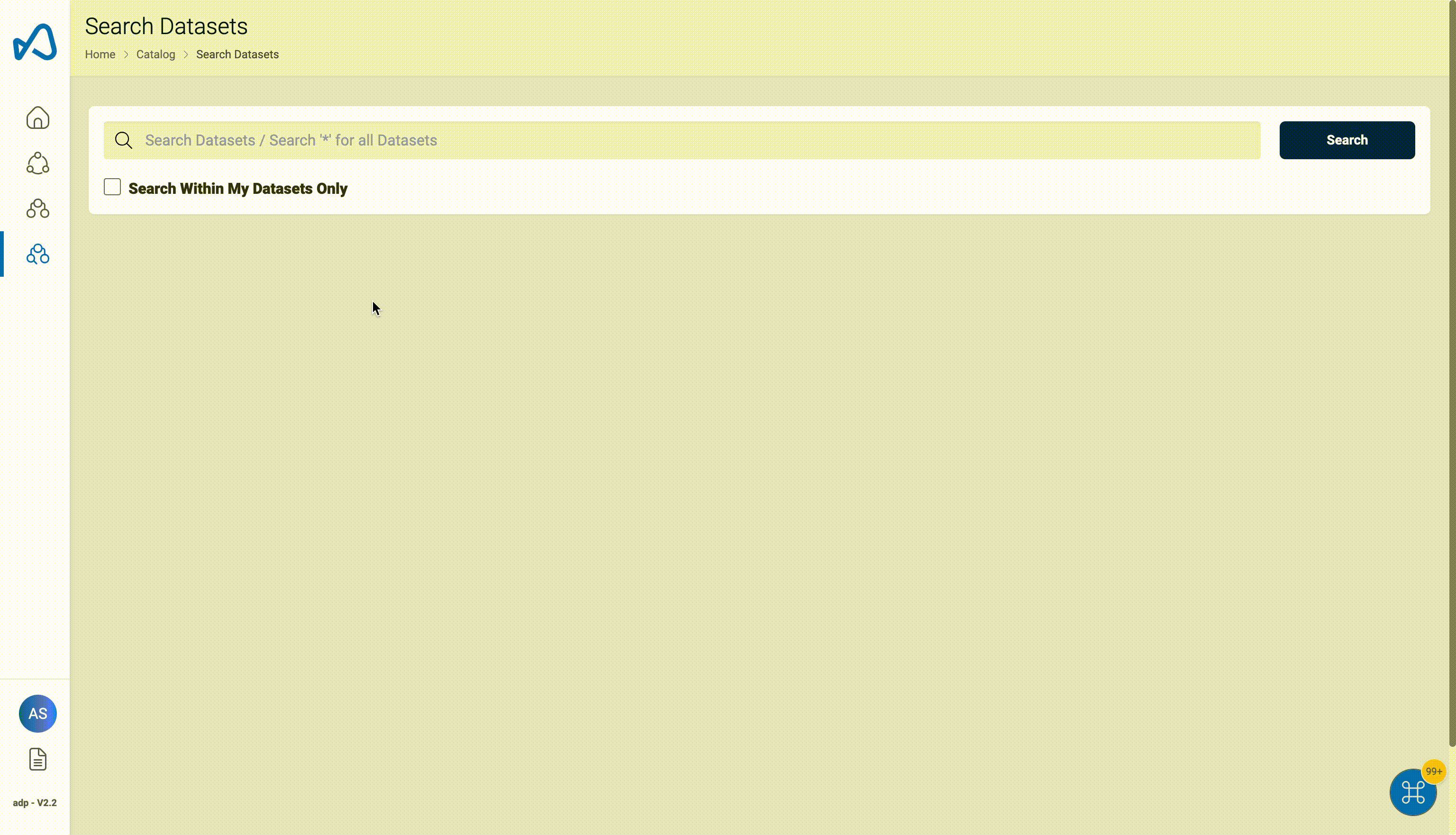
Switch Role
Switch Role functionality is enabled for users with more than one Role attached to them.
How to switch roles in Amorphic:
- Click on the User Profile icon
- Select
Switch Rolefrom the dropdown menu. - Pick a role from the list to switch to.
How to update user default-role?

The Update Default Role feature allows users who have more than one role to choose which role they want as their main role.
- Click on the User Profile icon located on the top right corner of the page.
- Select the
Profile & Settingsoption from the drop-down menu. - You will be taken to the
User Profilepage, where you will find theDefault Rolefield. - Click on the
Changebutton beside theDefault Rolefield. - A drop-down list of roles that the user is attached to will appear.
- Select one of the roles from the list to switch to it as the default role.
RBAC v2 Role Permissions Update
To simplify the process of creating, updating, and managing roles, the permissions structure has been streamlined. Instead of using multiple fine-grained permissions, users now select from three predefined permission levels for each service:
View: Grants basic access to view and list resources.
Manage: Allows for operational tasks like running jobs and generating reports.
Full Access: Provides complete control, including the ability to create, update, and delete resources.
Migration to the New Permissions Model
All existing roles will be automatically transitioned to the new permissions model, ensuring uninterrupted user activity. Please note that this migration is irreversible, and the previous detailed permissions will no longer be supported.
As part of the RBAC v2 update, several services have been consolidated into unified permissions to streamline complexity and improve the user experience. The table below presents a comparison of the old and new permissions:
| Old Service (Replaced) | New Service (Replacement) |
|---|---|
| connsapps | appflows |
| costmgmt-tags | cost-mgmt |
| groups | tags |
| athena-session-credentials, runquery, nl2sql | playground |
| systemdatasets, aws-roles, userdomains, whitelistips, usage, dataload-limits, custom-alert-emails, systemhealth, cost-explorer, cost-monitor, sysops, mailservers, saml, reports, service-limits, events, system-configs, user-agreements, systemalerts | system-settings |
As part of the migration, the following permissions have also been removed: users.list, users.view, roles.update
- There are no separate 'manage' permissions for roles. If a user has 'roles.view' access and is designated as a role manager for a specific role, they will have the ability to manage all aspects of that role.
- The 'users.view' permission has been removed, as listing basic user details is accessible to all users. To manage all users in the system and view their associated resources, a user must have the 'users.manage' permission.
- Following the migration, roles may potentially have no permissions if all previous permissions have been deprecated or replaced. Users are required to update the permissions for these roles in accordance with the new V2 model.