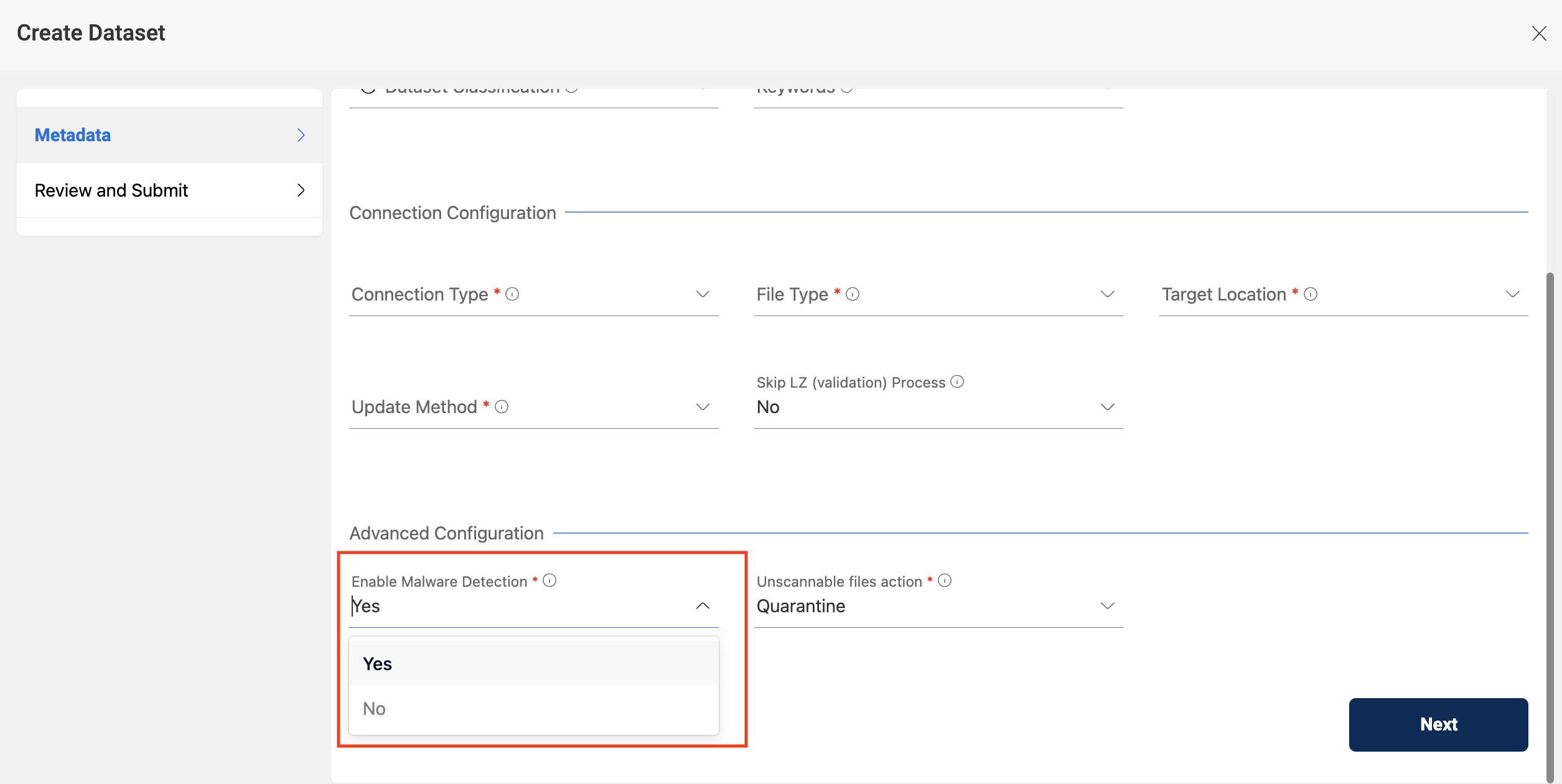
Enable Malware Detection
Amorphic application provides user with an option to detect malware in the files uploaded to the dataset. If the file has malware in it, it will be quarantined. All the file types Amorphic supports can be tested for malware.
The following picture depicts how to enable detection of malware
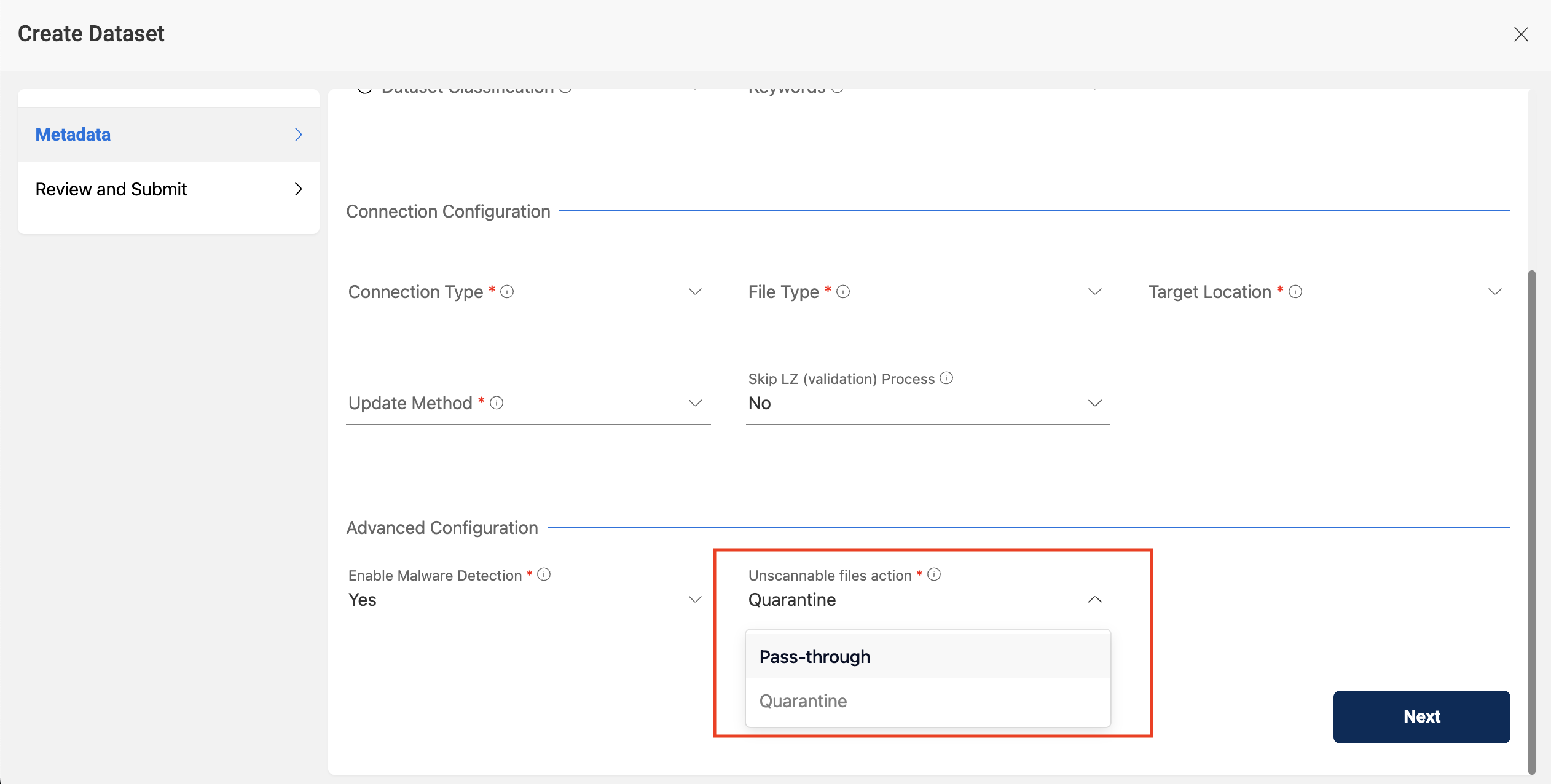
There is an option for user to ignore unscannable items and pass-through it to dataset if the user wants, for that user has to select
When the user selects option to detect malware, it becomes the first phase of data validation. If the file is malware free, it is moved to next phase of data validation else the file will be quarantined.
If the file is unscannable based on option selected by user whether to let it pass-through to the next phase of validation or quarantine it.
When the file is quarantined it is moved to a separate bucket in the AWS account where the Amorphic application is deployed. The bucket has a postfix -quarantine and the files are structured based on the domain and dataset they belong to.
These files won't be available to be viewed from Amorphic application, they are only available through AWS Console.
All the files from Quarantine bucket will be permanently deleted automatically in four weeks.
When an unscannable or a malware file is detected alerts will be send to Amorphic system-admins along with users subscribed to the dataset notifications.
If a file is larger than 300MB, unscannable file exception will be thrown. A file which is encrypted or compressed is also considered unscannable.
Amorphic application uses yara-python framework to detect malware in the files. yara-python requires yara rules to detect the malware. The yara-rules that are used in Amorphic are taken from the binaryalert repository in Github.
YARA files
Below are the YARA files that were used to detect malware
malware_macos_bella
Description: This file has a rule that will identify bella python tool presence
Rule: The rule has constant variable values which are related to bella tool and the YARA condition used raises exception if it encounters any one of the variable value.
malware_macos_macspy
Description: This file has a rule that will identify macSpy which is malware-as-a-service(MaaS)
Rule: The rule has constant variable values which are related to macSpy and the YARA condition used raises exception if it encounters any one of the variable value at the specified index.
malware_macos_marten4n6_evilosx
Description: This file has a rule that will identify EvilOSX which is pure python, post-exploitation, RAT (Remote Administration Tool)
Rule: The rule has constant variable values which are related to EvilOSX and the YARA condition used raises exception if it encounters any one of the 4 variable value out of 5 defined.
malware_macos_neoneggplant_eggshell
Description: This file has a rule that will identify EggShell which is post exploitation surveillance pentest tool written in Python.
Rule: The rule has constant variable values segregated into three sections and based on the strings encountered in file YARA ef"condition used raises exception.
malware_multi_pupy_rat
Description: This file has a rule that will identify pupy which is opensource cross platform rat and post-exploitation tool.
Rule: The rule has constant variable values which are related to pupy and the YARA ef"condition used raises exception if it encounters any one of the 3 variable value out of 6 defined.
malware_multi_vesche_basicrat
Description: This file has a rule that will identify cross-platform Python 2.x Remote Access Trojan (RAT).
Rule: The rule has constant variable values which are related to basicrat and the YARA ef"condition used raises exception if it encounters all of the 5 variable values.
malware_windows_apt_red_leaves_generic
Description: This file has a rule that will identify Red Leaves which is bases on opensource rat.
Rule: The rule has constant variable values which are related to Red Leaves and the YARA condition used raises exception if it encounters any one of the 2 variable value out of 15 defined.
malware_windows_apt_whitebear_binary_loader
Description: This file has a rule that will identify WhiteBear which contains a set of messaging and injection components that support continued presence on victim hosts.
Rule: The rule has constant variable values segregated into diff sections and based on the strings encountered in file, YARA ef"condition used raises exception.
ccleaner_backdoor
Description: This file has a rule that will identify backdoor in Ccleaner.
Rule: The rule has constant variable value which is related to Ccleaner Backdoor and the YARA ef"condition used raises exception if it encounters variable value that is defined.
malware_windows_moonlightmaze_cle_tool
Description: This file has a rule that will identify Moonlight Maze 'cle' log cleaning tool.
Rule: The rule has constant variable values which are related to Moonlight Maze 'cle' and the YARA ef"condition used raises exception if it encounters any one of the 3 variable value out of 6 defined.
malware_windows_moonlightmaze_custom_sniffer
Description: This file has a rule that will identify Moonlight Maze sniffer tools.
Rule: The rule has constant variable values which are related to Moonlight Maze sniffer and the YARA ef"condition used raises exception if it encounters any one of the variable values.
malware_windows_moonlightmaze_de_tool
Description: This file has a rule that will identify Moonlight Maze 'de' and 'deg' tunnel tool.
Rule: The rule has constant variable values which are related to Moonlight Maze 'de' and 'deg' tunnel and the YARA ef"condition used raises exception if it encounters any one of the 2 variable value out of 3 defined.
malware_windows_moonlightmaze_IRIX_exploit_GEN
Description: This file has a rule that will identify Irix exploits from David Hedley used by Moonlight Maze hackers
Rule: The rule has constant variable values which are related to Irix and the YARA condition used raises exception if it encounters any one of the variable value at the specified index.
malware_windows_moonlightmaze_loki
Description: This file has a rule that will identify Moonlight Maze Loki samples by custom attacker-authored strings
Rule: The rule has constant variable values which are related to Moonlight Maze Loki samples and the YARA ef"condition used raises exception if it encounters any 2 of the 11 variable values defined.
malware_windows_moonlightmaze_loki2crypto
Description: This file has a rule that will identify hardcoded DH modulus used in 1996/1997 Loki2 sourcecode
Rule: The rule has constant variable values which are related to Irix and the YARA condition used raises exception if it encounters any one of the variable value at the specified index.
malware_windows_moonlightmaze_loki2crypto
Description: This file has a rule that will identify hardcoded DH modulus used in 1996/1997 Loki2 sourcecode
Rule: The rule has constant variable values which are related to Moonlight Maze sniffer and the YARA ef"condition used raises exception if it encounters any one of the variable values.
malware_windows_moonlightmaze_u_logcleaner
Description: This file has a rule that will identify log cleaners based on utclean.c
Rule: The rule has constant variable values which are related to log cleaners and the YARA condition used raises exception if it encounters any one of the variable values.
malware_windows_moonlightmaze_wipe
Description: This file has a rule that will identify log cleaner based on wipe.c
Rule: The rule has constant variable values which are related to log cleaners and the YARA condition used raises exception if it encounters any two of the 4 variable values.
malware_windows_moonlightmaze_xk_keylogger
Description: This file has a rule that will identify Moonlight Maze 'xk' keylogger
Rule: The rule has constant variable values which are related to Moonlight Maze 'xk' keylogger and the YARA ef"condition used raises exception if it encounters any three of the 12 variable values.
malware_windows_pony_stealer
Description: This file has a rule that will identify Pony stealer malware
Rule: The rule has constant variable values which are related to Pony stealer malware and the YARA ef"condition used raises exception if it encounters all of the 10 variable values.
malware_windows_remcos_rat
Description: This file has a rule that will identify remote access Trojan (RAT) that can be used to fully control and monitor any Windows computer
Rule: The rule has constant variable values segregated into diff sections and based on the strings encountered in file, YARA ef"condition used raises exception.
malware_windows_t3ntman_crunchrat
Description: This file has a rule that will identify HTTPS-based Remote Administration Tool (RAT)
Rule: The rule has constant variable values which are related to Remote Administration Tool and the YARA ef"condition used raises exception if it encounters all of the 9 variable values.
malware_windows_winnti_loadperf_dll_loader
Description: This file has a rule that will identify loadperf. dll, is a modified version of its legitimate, similarly named counterpart—a Microsoft file
Rule: The rule has constant variable values which are related to Remote Administration Tool and the YARA ef"condition used raises exception if it encounters all of the 2 variable values.
malware_windows_xrat_quasarrat
Description: This file has a rule that will identify QuasarRAT
Rule: The rule has constant variable values segregated into diff sections and based on the strings encountered in file, YARA ef"condition used raises exception.
Challenges/Issues
Every effort has been made to neutralize false positive cases that a file might encounter. The rules are tuned to detect the malware but there are chances of encountering false positive cases.
User can also expect false negative cases, this can happen when the rules that are under use are not tailored for the malware that the file has in it. New generation malware cannot be detected as the rules that are used are based on the malware that was detected before 2018.
For more details about how the yara-rules are created and the documentation pertained to it, please checkout Yara Documentation